Configuring Data Center EVPN-VXLAN

Juniper Learning Byte: Configuring data center EVPN-VXLAN from start to finish
Watch as Juniper’s Zach Gibbs shows you the ins and outs of how to configure EVPN and VXLAN parameters in the data center. To note: this demo is most appropriate for users who have some familiarity with data center technologies.
You’ll learn
A step-by-step demo that takes you all the way through from topology to verification
How VXLAN tunnels will form in the configuration and where they are sourced from
Why you might not see a route for every host in the overlay (b/c EVPN does not pass routes until they are needed)
Who is this for?
Host

Transcript
0:02 [Music]
0:12 hello my name is zach gibbs and i'm a
0:14 content developer within education
0:17 services inside juniper networks and
0:20 today we will be going through the
0:21 configuring data center evpn vxlan
0:24 learning byte
0:27 all right so here is our topology we
0:29 have a few different devices uh five to
0:31 be exact we're five devices we will be
0:33 configuring and then there's two hosts
0:35 host one and host two uh the five
0:37 switches are spine one spine two leafs
0:40 one leaf two and leaf three and uh we do
0:44 have some parameters here on the left
0:45 you can see you can see the loopback
0:47 addresses for each switch spine1 is
0:50 192.168 100.1 spine2 is dot 2 leaf one
0:54 is dot 11 leaf 2 is 12 and leaf 3 is dot
0:58 13. and then with the hosts the hosts
1:00 are going to be in
1:01 vni 5099 both hosts and they're both
1:04 going to be in the same vlan and they're
1:06 both going to be in the same broadcast
1:08 domain the same subnet
1:10 and you can see here host one has
1:11 10.1.1.1
1:13 24 and host 2 has 10.1.1.2
1:16 24.
1:17 and what we're doing here or what we
1:19 want to do is we want to enable
1:21 communication between host 1 and host 2
1:24 by configuring evpn vxlan
1:27 and something else to point out here is
1:29 that this is the overlay network i
1:30 wanted to show this first and that
1:33 there's ibgp in the fabric that is
1:37 passing evpn routes around so just keep
1:39 that in mind
1:40 and so the overlay network is currently
1:43 working and functioning and well
1:45 technically it's not passing the routes
1:46 around yet because we haven't set up
1:48 evpn vxlan but it's set up to do so the
1:50 ivgp sessions have family evpn signaling
1:54 configured for them and then in the next
1:56 slide this slide shows how the vxlan
1:59 tunnels will be forming and you can see
2:01 here that
2:03 leaf 1 and leaf 3 since they have the
2:05 directly connected host devices they
2:07 will be forming vxlan tunnels to every
2:09 other device
2:11 and as you can see here leaf one will be
2:13 forming a vxlan tunnel with spine one
2:15 and then spine two and leaf two and also
2:18 leaf street and then you can see leaf
2:20 three is doing the same thing it's
2:21 forming a tunnel with leaf two leaf one
2:24 spine one and spine two
2:27 all right so here is the cli for spine
2:29 one and the first place we need to go is
2:31 the switch options and here we need to
2:34 configure the vtep source interface it's
2:37 going to be the loopback interface
2:38 and this works well because what happens
2:41 here is
2:42 the vxlan tunnels will be
2:44 sourced from the loopback and those
2:47 loopback
2:48 interfaces or the routes associated with
2:49 the loopback interfaces are being passed
2:52 around in the underlay network and so
2:54 we'll we will have reachability to those
2:57 routes because of that
2:59 and so next we need to configure the
3:00 route distinguisher that's going to be
3:02 six four six six five coin one and the
3:06 autonomous system that we're using here
3:08 is six four six six five uh that was
3:11 shown in the topology but i did forget
3:13 to point that out and so what we can do
3:16 here is we can do the same route
3:17 distinguisher calling something else on
3:19 each of the devices
3:21 and so spine 2 is going to be 6 4 6 6 5
3:24 colon 2 and leaf 3 is going to be 6 4 6
3:27 6 5 colon 3 and so forth and then we
3:30 need to set the vrf target and that's
3:32 going to be target colon it's going to
3:34 be based off of the autonomous system
3:36 number again and we're going to say 101
3:38 and that just needs to match on all the
3:40 switch devices here
3:42 and then we need to complete that
3:45 configuration on the other devices as
3:47 well and so the only thing that's going
3:48 to really change here is the route
3:50 distinguisher so what will be nice to do
3:52 is
3:55 i will
3:57 copy these commands out and then just
4:00 paste them in and make a quick change
4:01 where necessary
4:04 okay so let's go to spine2
4:06 and let's paste that in
4:09 and so we'll change the route
4:11 distinguisher to colon2
4:13 and then let's go to leaf one
4:16 and same deal
4:20 and we'll change the rod extinguisher
4:22 again to be something unique
4:24 and then let's go to leaf two and do the
4:28 same thing here
4:30 and change that route extinguisher to
4:32 something unique
4:34 and then let's go to leaf three
4:37 and do the same thing
4:40 and again change that to a unique value
4:43 for the route distinguisher okay so
4:44 let's jump back to spine1 and then next
4:47 we need to configure the
4:48 evpn protocol parameters
4:53 and then within here we need to set the
4:55 encapsulation to vxlan since we will be
4:57 using vx land tunnels and then we can
5:00 set the extended
5:02 vni list and you can specify the
5:05 specific vnis we're using and we are
5:08 using
5:08 5099 for the vni or you could use the
5:11 shortcut of all if there's
5:14 more than just one or a whole bunch or
5:16 whatever save you some time so we're
5:18 just going to say all granted we only
5:20 have one so it's not really saving us
5:21 much time but i did want to point that
5:23 out
5:24 and then let's do the display set again
5:27 and we'll copy this to the other devices
5:31 in the data center
5:35 and it's no changes so this will be
5:38 quick and easy
5:42 and then there's leaf three all right so
5:43 let's go back to spine one
5:46 and then we need to configure the vlan
5:49 and we set we'll call this v10 because
5:52 it's going to be vlan
5:53 use the vlan id of 10 and then we need
5:55 to set the vxlan vni that this vlan will
5:58 be using to 5099
6:04 and we'll again copy this information
6:06 out and copy it to the other devices
6:09 and there's no changes there so we can
6:10 simply just copy it in
6:13 that's leaf one leaf two
6:15 and leaf three
6:17 and
6:18 then on spine one let's go ahead and
6:20 commit the configuration there's nothing
6:21 else we need to do there
6:23 spine two same thing
6:25 and leaf one we'll need to make a change
6:28 leaf two we don't so let's go ahead and
6:29 commit the configuration and then jump
6:31 back to leaf one now recall that leaf
6:34 one is directly connected to host one on
6:37 its xe004
6:40 interface
6:45 you can see here it's configured but
6:48 it's not configured as a member of that
6:50 vlan we just created v10 so we need to
6:52 set that as a member of that vlan
6:59 and we'll set v10
7:02 then we can commit the configuration
7:03 there and we'll jump to leaf three and
7:05 do the same thing
7:11 you can see here it is
7:12 configured but not all the way
7:18 and then
7:20 let's go ahead and commit the
7:21 configuration
7:23 and then let's jump back to leaf one and
7:26 have a look at some things see what we
7:28 can see here
7:30 see if there's any vxlan tunnels up
7:34 looking for remote endpoints anything
7:36 coming in and we do what do we have here
7:38 we have something coming in from leaf
7:40 three recall that the loopback address
7:43 of leaf three
7:44 is 192 168 100.13
7:48 and that's exactly what we want to see
7:50 and we can see it's coming in
7:52 from that address and we can see the vni
7:54 id as well
7:56 and we see the vtep interface that is
7:58 being used and that's perfect that's
7:59 exactly what we want to see and you can
8:01 see the
8:02 loopback information there shown for the
8:05 source vtep ip
8:07 and so that looks good that's exactly
8:08 what we want to see now we can change
8:10 this command to source
8:13 and we have some information as well we
8:15 can see the vlans that are are present
8:17 you couldn't see that in the previous
8:19 output so you can see the vlan name is
8:20 v10 and then the vlan id is 10. that
8:23 looks good and so yeah everything looks
8:25 good here that's how we should see it
8:26 and so with that let's run those
8:28 commands
8:29 or at least one of them on the other
8:30 devices to show you what we have here
8:37 and you can see here the output's a
8:38 little different and recall remember i
8:40 said that
8:41 the leaf one and leaf three devices
8:43 would be forming vxlan tunnels with
8:45 every device in the switch fabric and
8:48 you can see that here now if we jump
8:50 back to leaf one we only saw one tunnel
8:52 well why is that well that's because no
8:55 other devices besides leaf three is
8:58 forming tunnels so we only have one from
9:00 leaf three but on spine one that we see
9:02 here we see the two tunnels we see it
9:04 from leaf one and from leaf three
9:07 and that's exactly what we should be
9:08 seeing now one other thing i do want to
9:10 point out here and i did mention it
9:12 briefly just a few minutes ago is the
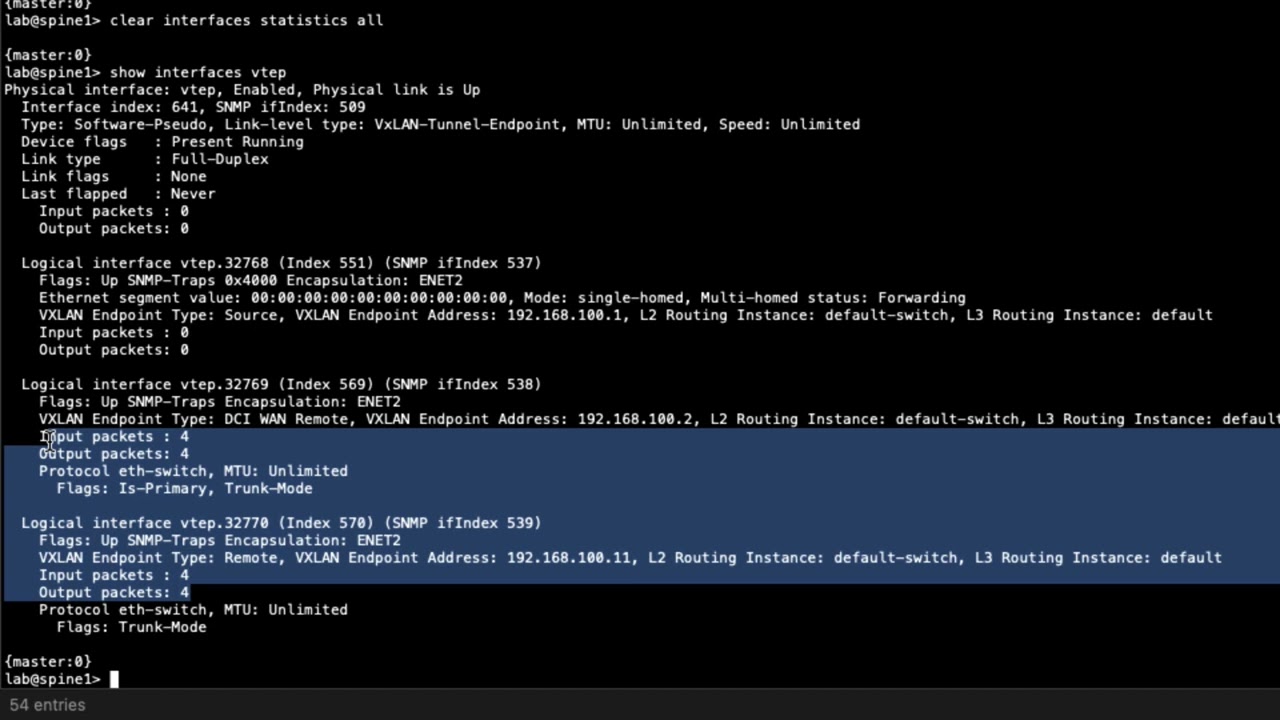
9:14 vtep interfaces these are the vtep
9:16 interfaces that are being used and the
9:19 nice thing about this is you can look at
9:20 the vtep interfaces to get more
9:22 information and let's do that now let's
9:24 do show
9:26 interface vtep
9:28 to 327.69
9:31 and you can see here vxlan tunnel
9:34 endpoint type remote that's good
9:37 where it's coming from
9:39 and another thing that i do like to
9:41 point out is the input and output
9:43 packets once you start sending traffic
9:45 you should see this incrementing if it's
9:47 not incrementing or only the input or
9:49 only the output is incrementing then you
9:51 definitely have some problems so keep
9:52 that in mind so you want to look for
9:54 that
9:55 and we can jump to spine too
10:00 and we'll see the similar information
10:01 and even on leaf two we'll see similar
10:03 information
10:08 and so with that let's uh what else
10:10 should we look at let's look at let's go
10:12 back to leaf one i do want to show it on
10:14 leaf three real quick that same command
10:18 and you can see here it's basically the
10:20 reverse it's coming from leaf one
10:23 the source is leaf three so things look
10:25 good there it's using that vtep
10:26 interface
10:28 and so
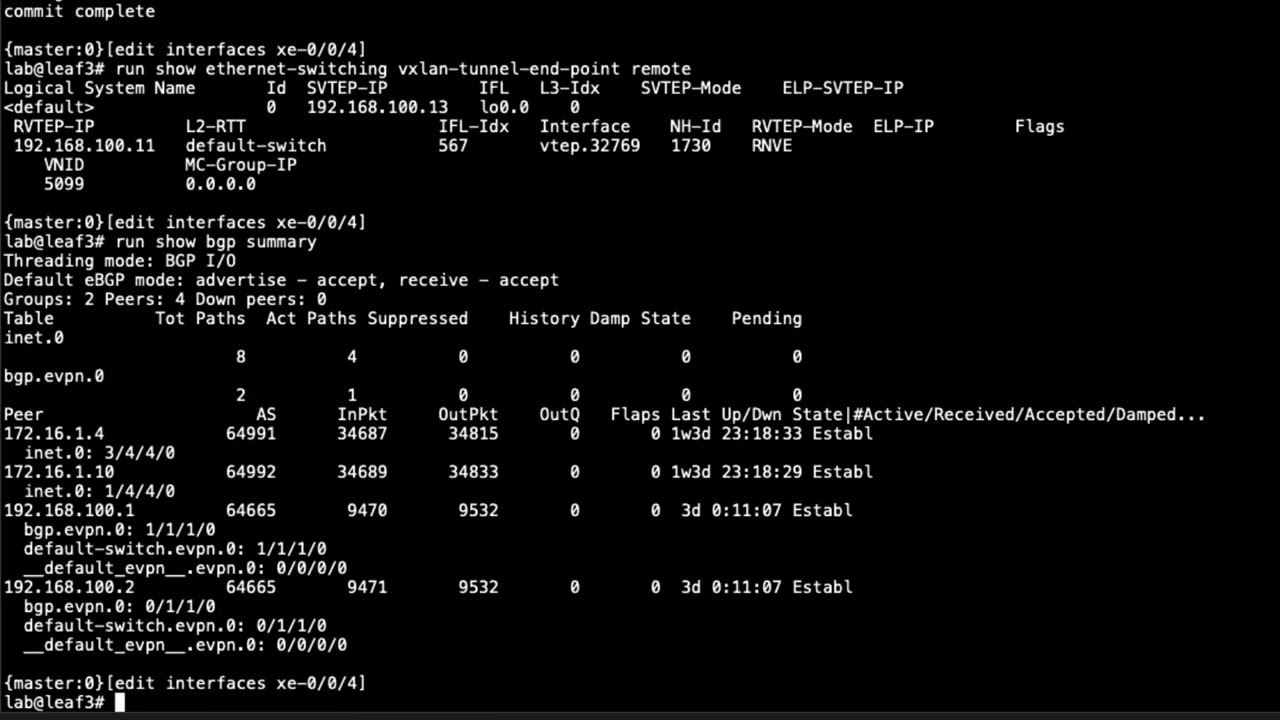
10:29 uh with this let's do the run show bgp
10:32 summary command so you can see here in
10:34 this output that we are receiving
10:37 a single bgp evpn route or rather in the
10:42 bgbevpn.0 table and also on the default
10:47 switch.evpn.0 table as well
10:49 now that might seem a little odd because
10:50 we
10:51 have at least two hosts and so there
10:53 should be at least two routes right well
10:56 how it works is there is going to be
10:58 some sort of routing shared and that has
11:00 nothing to do with the hosts and that's
11:02 that single route you're seeing
11:04 and it isn't until
11:06 we start sending traffic between the
11:08 hosts that more routes will be passed
11:10 and that's because evpn how it works is
11:12 it's not going to pass the routes until
11:14 they're needed so keep that in mind and
11:16 also i do want to point out that 192 168
11:18 100.1 that's spine1 and the 192.168
11:22 100.2 that is spine2 they are rut
11:24 reflectors and so that's why we're only
11:26 seeing those two in the overlay network
11:28 and let's ping host two you can see host
11:31 two is able to talk to host one and
11:33 let's do the reverse on host two as well
11:35 and so we have traffic flowing so let's
11:37 go back to leaf three and let's run that
11:39 same command and you can see here that
11:41 we do have we see
11:44 in the default switch you know we see
11:45 this change here because this is what's
11:47 coming from
11:48 dot one
11:49 which is leaf one and so if we scroll
11:51 back up you can see here that
11:54 we do have just one route but now we
11:56 have three routes going back you know so
11:59 some routes are being passed and we can
12:00 look at leaf one we do the same thing
12:04 and you can see that i misspoke when i
12:06 was looking at leaf one i said dot one
12:08 here is uh is leaf one that's not that's
12:10 spine one because we have route
12:12 reflectors sorry i got a little confused
12:13 there so this is spine one spine one is
12:16 reflecting the route spine two is also
12:18 reflecting the routes but it's being
12:19 hidden that's why you have that and so
12:21 that's what you see here now more routes
12:23 are being reflected
12:24 and you can see from spine one that we
12:27 are getting three routes instead of one
12:28 route and you can see on spine
12:30 two
12:32 the spine two session that those routes
12:34 are being hidden because we're already
12:35 getting them from spine one and so we
12:37 jump to
12:39 leaf one and we'll see the same thing
12:40 here we'll see that we're getting routes
12:43 from spine one
12:45 and we're getting three of those routes
12:47 uh evpn routes
12:49 and so let's actually look at those
12:50 routes
12:53 let's do bgp.evpn.0
12:56 and you can see the routes that we're
12:58 getting here
12:59 you see that they are type 2 and type 3
13:02 routes
13:03 and if i scroll up here i believe this
13:05 is the route that is coming from
13:09 host two let's jump to host two real
13:11 quick cause i think that's its mac
13:12 address right there if i remember right
13:14 so let's look at host two
13:17 kill this ping
13:19 and uh
13:23 let's look at the mac address here and
13:25 so
13:26 okay this is the mac address that we're
13:27 using on this interface it's
13:30 for a0 so let's jump back to leaf one
13:32 and i think that's what we see there yep
13:34 4 a0 so that's exactly what we have so
13:36 that is that route and then we can look
13:38 at the
13:42 look at the what table is the default
13:46 switch evpn evpn0
13:48 and you can see the mac and ip rouse the
13:51 the two and threes kind of similar
13:53 information what you saw before and so
13:55 that's that route for host two and
13:57 that's from leaf one
13:59 and then i want to show let's look at
14:01 the evpn
14:03 database
14:05 and here in the evpn database you see
14:07 that
14:08 we have
14:10 this is leaf threes
14:12 and that is host whose mac address
14:14 and you can see the ip address we know
14:16 that's host 2's ip address and the
14:18 active source is
14:20 leaf 3 and so that's exactly we want to
14:22 see then here you'll see active source
14:24 for this route or this database entry
14:27 is pointing out xe004 and that's the
14:29 local interface on the leaf so that
14:31 means
14:32 that this is host one's mac address and
14:34 you can see host one's ip address as
14:36 well
14:37 and i want to jump back to host 2 and
14:40 get that ping going again because i do
14:41 want to show one other quick thing
14:43 so
14:44 recall i said something about that vtep
14:46 interface so i do want to show the
14:48 ethernet switching vxlan remote command
14:51 again and then we're going to look at
14:53 that interface
15:00 and you can see here we see the packets
15:02 there's packets going in and out of that
15:04 interface
15:05 if we look at that again you can see
15:06 it's incrementing and that's great that
15:08 means that that traffic is going in and
15:10 out of that vxlan tunnel or the vxlan
15:13 tunnels and so everything definitely
15:15 looks good and is functioning well with
15:18 evp and vxlan and host one and host two
15:20 can communicate without any problems
15:23 so that does bring us to the end of this
15:25 learning byte in this learning byte we
15:26 demonstrate how to configure and verify
15:28 evpn vxlan in the data center so as
15:31 always thanks for watching
15:34 visit the juniper education services
15:36 website to learn more about courses
15:39 view our full range of classroom online
15:42 and e-learning courses
15:44 learning paths
15:46 industry segment and technology specific
15:48 training paths
15:50 juniper networks certification program
15:53 the ultimate demonstration of your
15:55 competence
15:56 and the training community from forums
15:58 to social media join the discussion