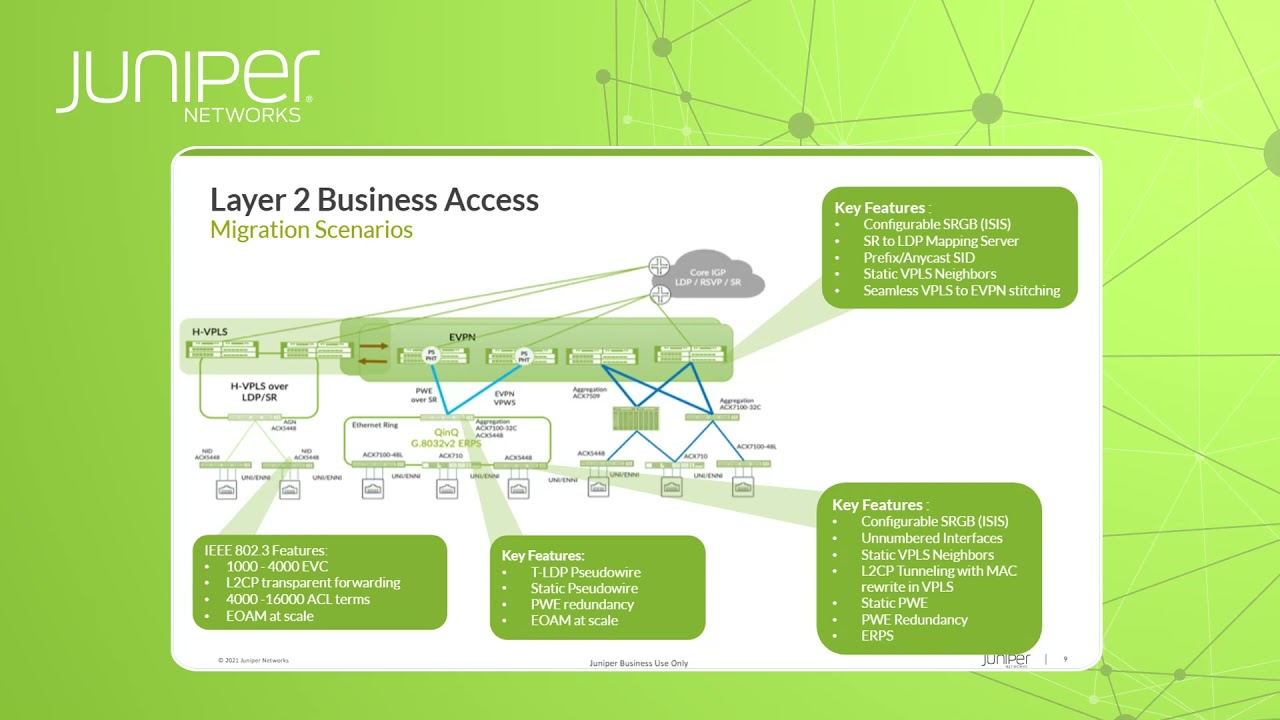
Exploring 5G Security Strategy Considerations

5G security — it matters and here’s how Juniper can help.
Juniper can help strengthen your 5G security by empowering the network to identify and respond to threats before they can do harm. Juniper’s Albert Lew explains how in this 5G, security-focused episode of Light Reading.
You’ll learn
How 5G security compares to previous mobile generations
The ways in which Juniper Insights detects malicious threats encrypted in 5G traffic
How Juniper helps network operators analyze traffic to detect and quickly respond to threats
Who is this for?
Host

Guest speakers

Transcript
00:06 i'm phil harvey i'm the editor
00:07 at light reading and i'm joined on the
00:09 presentation today by
00:11 albert liu from juniper networks hi
00:13 albert how are you
00:14 good how are you doing phil i'm doing
00:16 great thanks for uh
00:17 making some time for us today um i have
00:20 a lot of questions well not a lot but i
00:22 have a few questions very important
00:23 questions about
00:24 um 5g and security so
00:28 um one of the uh uh
00:31 first things i think that that comes up
00:33 when we're thinking about
00:34 how the world is changing with 5g
00:36 networks coming online everywhere
00:38 and i read the other day that uh
00:42 there's something like more than half of
00:44 americans are
00:45 or you know their next purchase is their
00:48 next phone purchase is definitely going
00:50 to be
00:51 a 5g phone um so it's really catching on
00:55 i guess uh the first question in terms
00:57 of security is how does 5g compare to
01:00 all of the other mobile generations 3g
01:02 4g and so on when it comes to
01:05 network security well that's a great
01:08 question phil
01:09 so with 5g we're seeing that there's
01:12 going to be a lot
01:13 more applications that service providers
01:16 are going to want to
01:17 provide to their customers they're going
01:20 to need to have
01:21 a more responsive network and the way
01:23 that they're going to do this
01:24 is to transform the network from a
01:28 centralized deployment which we've seen
01:30 in 2g 3g and 4g into a distributed
01:34 deployment
01:35 and they're also going to be moving from
01:37 really
01:38 a physical appliance based design and
01:41 architecture to one that's much more
01:43 software heavy with virtual machines and
01:45 containers
01:46 and they're going to take services and
01:48 applications and move them
01:51 into these distributed edge clouds where
01:53 they're going to have
01:54 software at the very edge and what that
01:56 means
01:57 is that the security is also going to
02:00 need to be distributed in other words
02:02 security is going to need to follow
02:04 where the workload is
02:06 in reality this is not going to be you
02:08 know either it's centralized or it's
02:11 distributed
02:12 or physical or virtual uh because
02:14 there's going to be a mix of all of
02:15 these things in
02:16 any service provider network it's going
02:18 to be both and which means
02:21 we're going to have to have lots of
02:22 different form factors for security
02:25 whether it's hardware software container
02:27 or virtual machine based i was talking
02:29 to
02:30 one of our customers recently and even
02:32 though they are
02:33 all in quote unquote all in on software
02:37 deployment for their 5g network
02:39 they're also looking at parts of their
02:41 network where they're acknowledging
02:42 that they have to do it in hardware so
02:45 the real challenge is
02:46 how do you now have consistent security
02:50 and apply that security across a mix
02:54 of different locations as well as
02:56 different technologies for
02:58 deployment in other words how do you
03:00 have a unified policy mechanism
03:02 that can be applied across your entire
03:04 network consistently and automatically
03:07 and then when you have challenges in the
03:09 network can we be reliable and resilient
03:12 so that even if you may have many
03:14 different types of security deployed in
03:16 the network
03:17 can they somehow back up each other so
03:20 at juniper
03:21 we've really been prioritized on
03:23 unifying the security policy management
03:25 to have a consistent set of security
03:27 policies
03:28 across all forms of security to ease
03:32 that transition
03:33 in that transformational journey service
03:34 drivers are making from a centralized
03:37 purely physical
03:38 model to one that is a mix of
03:40 centralized and distributed
03:42 and now mixes software together with
03:44 physical and
03:45 while we're doing that we're also
03:46 looking to make sure that we can
03:48 support multi-node high availability so
03:51 that we can have
03:52 heterogeneous devices and instances
03:56 and software back up both back up each
03:59 other from a physical
04:00 virtual and container standpoint to get
04:03 more resiliency for
04:05 service providers and their customers
04:08 wow okay so there's a lot going on there
04:10 there's definitely
04:11 some technology challenges that uh
04:14 uh that you have to uh kind of adapt to
04:16 as we move from like you said that more
04:18 centralized
04:19 uh way of handling security to a more
04:21 distributed more software friendly or
04:23 software-centric i guess way of doing it
04:26 um you know i i guess one of the things
04:28 i've heard about 5g networks in terms of
04:31 the security side is that they allow for
04:33 a stronger encryption or better
04:35 encryption
04:36 is it true that traffic is automatically
04:39 um encrypted on these networks or how
04:41 exactly is that handled
04:44 well you know some traffic is encrypted
04:46 automatically and and some is not
04:49 and traditionally traffic has been
04:52 uh encrypted on the backhaul in the
04:54 network so that we could
04:56 improve integrity and data
04:58 confidentiality in an
05:00 insecure part of the network but
05:02 security is more than just data privacy
05:04 right we've seen in recent years
05:06 there's been a rising trend where cyber
05:08 criminals
05:09 will hide malicious threats such as
05:11 malware inside encrypted traffic
05:13 which can make it harder to detect so if
05:16 you can't
05:16 see these types of threats then it's
05:19 really hard to protect
05:20 against them so the first thing is
05:22 visibility
05:23 you have to have visibility before you
05:25 can identify threats and stop them
05:28 but usually this requires a very brute
05:31 force
05:31 resource intensive approach for instance
05:34 you're just going to
05:35 decrypt everything that comes into the
05:37 network and while this is okay
05:39 for certain parts of the network and
05:40 there's kind of specialized offerings to
05:42 do that
05:43 it's really tough to do this across the
05:45 network everywhere
05:46 and it's really hard now in 5g because
05:48 the core networks
05:50 and oran are going to support ssl and
05:53 tls encryption everywhere in their
05:55 network so there's got to be
05:56 a better way to do this so that it's
05:59 less expensive and also
06:01 we can maintain the performance
06:02 customers expect so fortunately with
06:05 innovation
06:06 that we've done at juniper networks
06:07 including our encrypted traffic
06:09 insights capability we can enable our
06:12 customers as such as service providers
06:14 to detect
06:15 malicious threats that are hidden in
06:17 encrypted traffic
06:18 without brute force opening up that
06:21 traffic and seeing what's going on
06:23 and we're doing that by analyzing the
06:25 patterns of those connections
06:27 with machine learning and constantly
06:29 updating that in the cloud
06:31 and since we don't have to actually
06:32 crack open
06:34 all the traffic to look at it and since
06:36 we also do not take what i would call
06:39 an ineffective way of looking at
06:42 the statistical statistical
06:45 behavior and profile of the traffic
06:47 we're actually able to with a high
06:49 degree of certainty
06:50 find these threats that are in encrypted
06:53 traffic without
06:54 any impact to latency or performance
06:58 yeah that's and that's incredibly
06:59 important because both of those are
07:02 you know the reason for being for 5g
07:03 networks
07:05 right great okay good good to hear on
07:07 that front
07:08 um one last question about security and
07:11 5g networks
07:12 is you know what are some of the unique
07:14 challenges
07:15 that iot presents in a in the context
07:18 of a of you know a 5g network or what
07:22 you know what challenges should network
07:23 operators be looking for and then
07:25 what um you know i guess as a response
07:28 to those challenges what what can
07:29 operators do
07:32 well of course iot introduces a
07:35 multiple magnitude of order increase in
07:38 the number of devices
07:40 that are connected to the network so
07:42 that's probably
07:43 uh the biggest challenge it's also the
07:45 best news for
07:46 consumers and businesses because uh
07:50 but on the other hand cyber attackers
07:53 can take advantage of the fact there's
07:54 many of these devices right
07:56 and these devices are harder to secure
07:59 and they're going to become good targets
08:02 for attackers to leverage
08:04 and the reason for that is because
08:06 there's less effort that goes into
08:08 making sure
08:09 that the software in these devices comes
08:12 from well-known places
08:14 and can be really trusted right so now
08:16 we have a very interesting problem
08:19 in which we have attacks that
08:22 are could be coming from the inside of
08:25 the network because
08:26 before we've really seen ddos attacks
08:28 coming from the outside
08:29 with iot what do you do about these
08:32 attacks are coming from the inside
08:34 what happens if your subscribers what
08:36 happens if the iot devices they're using
08:38 as part of their subscriptions
08:40 become weaponized and then they launch
08:42 attacks either on the outside world or
08:45 maybe
08:45 inside the service provider and when
08:47 this happens
08:48 trying to figure out and trace back
08:50 these attacks
08:51 can cause a lot of challenges both in
08:54 time
08:54 and lost reputation in lost revenue
08:58 so right now mobile service writers have
09:01 a very difficult time
09:03 trying to understand what's happening
09:05 because
09:06 they just don't have the tools to be
09:08 able to to see these types of problems
09:11 so the network is really important to be
09:13 able to identify these threats
09:16 and to analyze the traffic so that we
09:18 can figure out
09:20 what is just like higher volume of
09:22 traffic for instance
09:24 national holidays lots more traffic
09:26 that's kind of okay
09:28 right but uh attacks are coming from the
09:31 inside and they could be mounted towards
09:33 a very particular target
09:35 that can be hard to detect so juniper
09:37 secure
09:38 juniper connected security our strategy
09:41 for building a threat aware network
09:42 is really to uh its goals
09:46 are to safeguard users applications and
09:48 infrastructures
09:49 from client to cloud everywhere across
09:51 the network
09:52 and one of the ways that we're doing
09:54 this is with our
09:56 ddos solution that we have partnered
09:58 with carrero network security and it can
10:01 help service providers identify these
10:04 inside-out attacks we also have
10:06 capabilities such as security
10:08 intelligence
10:09 which can look for activities like
10:12 weaponization of malware
10:14 reconnaissance also infiltration of
10:17 malware that may be coming from places
10:18 that you don't expect
10:20 and by bringing the power of the entire
10:22 network we're not
10:23 requiring we'll just call them expensive
10:26 firewalls for the purpose of
10:28 in these very wide edges for the mobile
10:31 service providers network it's just not
10:33 cost effective
10:34 to put firewalls there you have to
10:36 really use the entire network the
10:38 network infrastructure to detect
10:40 and respond to threats and do that in a
10:42 performant way that
10:44 also preserves the qos for the service
10:46 provider
10:47 and this is what we mean by connected
10:49 security really using the whole network
10:51 as a muscle to identify
10:53 and stop those threats and and we think
10:55 that's going to be key
10:56 to offering a high quality secure iot
10:59 service
11:00 yeah that's great too because it it um
11:03 you know it's
11:04 nearly impossible to uh economically to
11:08 put security on individual iot devices
11:10 all over the place we've sort of
11:13 seen that and that would kind of uh that
11:15 would kind of take all the fun out of
11:16 iot to begin with
11:17 um so having having the network uh help
11:20 you
11:20 uh identify and and reduce the threats
11:23 is is is a is a
11:24 a great plan and uh uh albert liu thanks
11:28 so much for
11:28 uh walking us through a few uh uh
11:30 scenarios and
11:31 and sort of uh things that juniper is
11:33 working on when it comes to 5g security
11:36 yeah thanks phil and it's been a
11:37 pleasure talking to you about this
11:39 look forward to talking to you soon