What is IDS and IPS?
What is IDS and IPS?
Intrusion detection is the process of monitoring your network traffic and analyzing it for signs of possible intrusions, such as exploit attempts and incidents that may be imminent threats to your network. For its part, intrusion prevention is the process of performing intrusion detection and then stopping the detected incidents, typically done by dropping packets or terminating sessions. These security measures are available as intrusion detection systems (IDS) and intrusion prevention systems (IPS), which are part of network security measures taken to detect and stop potential incidents and are included functionality within next-generation firewalls (NGFW).
What are the benefits of IDS/IPS?
IDS/IPS monitors all traffic on the network to identify any known malicious behavior. One of the ways in which an attacker will try to compromise a network is by exploiting a vulnerability within a device or within software. IDS/IPS identifies those exploit attempts and blocks them before they successfully compromise any endpoints within the network. IDS/IPS are necessary security technologies, both at the network edge and within the data center, precisely because they can stop attackers while they are gathering information about your network.
How does IDS work?
Three IDS detection methodologies are typically used to detect incidents:
- Signature-based detection compares signatures against observed events to identify possible incidents. This is the simplest detection method because it compares only the current unit of activity (such as a packet or a log entry to a list of signatures) using string comparison operations.
- Anomaly-based detection compares definitions of what is considered normal activity with observed events in order to identify significant deviations. This detection method can be very effective at spotting previously unknown threats.
- Stateful protocol analysis compares predetermined profiles of generally accepted definitions for benign protocol activity for each protocol state against observed events in order to identify deviations.
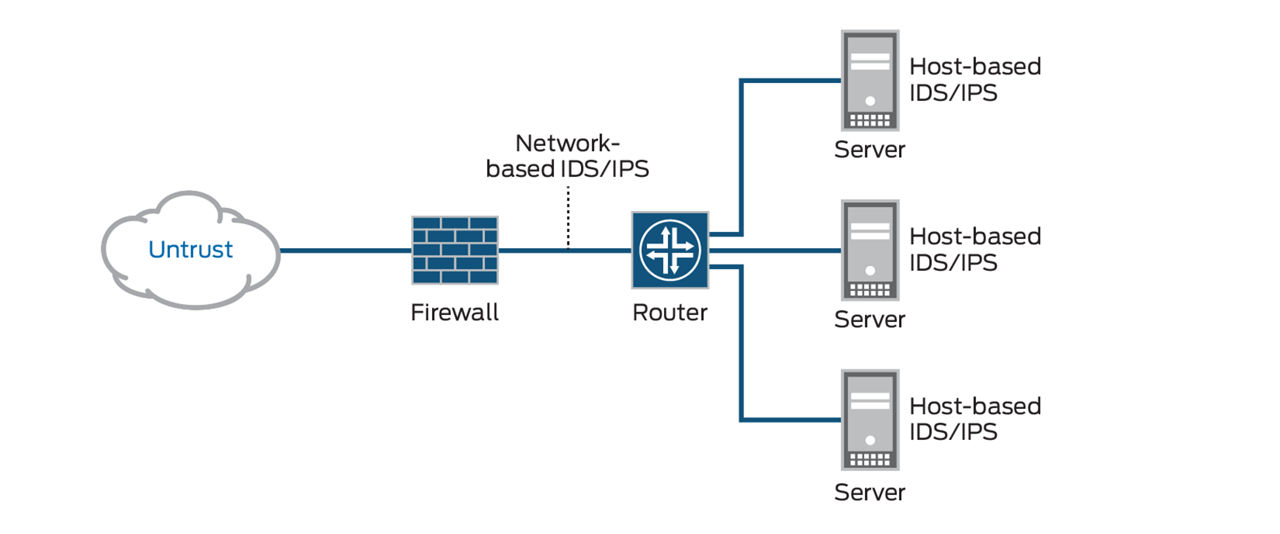
What Can You Do with IDS/IPS?
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) constantly watch your network, identifying possible incidents and logging information about them, stopping the incidents, and reporting them to security administrators. In addition, some networks use IDS/IPS for identifying problems with security policies and deterring individuals from violating security policies. IDS/IPS have become a necessary addition to the security infrastructure of most organizations, precisely because they can stop attackers while they are gathering information about your network.
Juniper's IDS and IPS
Juniper Networks SRX Series Firewalls, including the vSRX and cSRX, are fully equipped for intrusion detection and prevention (IDP) services. You can selectively enforce various attack detection and prevention techniques on the network traffic passing through your chosen SRX Series device or Secure Edge service, which provides firewall-as-a-service. You can define policy rules to match a section of traffic based on a zone, a network, or an application, and then take active or passive preventative actions on that traffic. The SRX Series and Secure Edge service both contain robust and continuously updated IPS signatures to secure networks against attacks. The SRX Series can forward IDP logs to any security incident and event management systems (SIEMs), such as Juniper Secure Analytics (JSA).
IDS and IPS FAQs
Is a firewall an IDS or IPS?
Yes. True next-generation firewalls contain IDS and IPS functionality. However, not all firewalls are next-generation firewalls. Also, a firewall blocks and filters network traffic, while IDS and IPS detect and alert or block an exploit attempt, depending on configuration. IDS and IPS act on traffic after the firewall filters the traffic, according to configured policy.
How are IDS and IPS implemented?
An Intrusion Detection System (IDS) is responsible for identifying attacks and techniques and is often deployed out of band in a listen-only mode so that it can analyze all traffic and generate intrusion events from suspect or malicious traffic.
An Intrusion Prevention System (IPS) is deployed in the path of traffic so that all traffic must pass through the appliance to continue to its destination. Upon detection of malicious traffic, the IPS breaks the connection and drops the session or traffic.
Can an IPS block traffic?
Yes. An IPS constantly monitors traffic for known exploits to protect the network. The IPS then compares the traffic against existing signatures. If a match occurs, the IPS will take one of three actions: 1) detect and log the traffic, 2) detect and block the traffic, or 3) (the recommended option) detect, log, and block the traffic.
What can an IDS detect?
An IDS detects threats based on patterns of known exploits, malicious behaviors, and attack techniques. An effective IDS also detects evasive techniques attackers use to hide exploits, such as remote procedure call (RPC) fragmentation, HTML padding, and other types of TCP/IP manipulation.
Learn more about what Juniper IDS/IPS can detect and block on our Signatures page.
Can an IPS prevent DDoS?
An IPS can prevent certain types of DDoS (distributed denial of service) attacks. For example, application denial of service (AppDoS) attacks are one of the threat categories that IPS functionality can identify and protect against. However, volumetric DDoS threats require a dedicated solution like Juniper’s Corero DDoS offering.
What IDS and IPS technologies, solutions, and products does Juniper offer?
Juniper offers both IDS and IPS solutions via a single software subscription deployed on any of Juniper’s next-generation firewall products and services: physical, virtual, and containerized SRX firewalls, or as a service within Juniper Secure Edge.

